Cyber Security Incident Handling Guide
Incident Handling Steps

(Source: NIST.SP.800-61r2)
According to the recommendations published by NIST, cyber incident response processes should be handled in 4 steps. These steps are as follows:
Preparation
Detection & Analysis
Containment, Eradication & Recovery
Post-incident activity
Preparation
The preparation step covers the preparations made before intervening in cyber security incidents. The preparations to be made in this step ensure that the cyber incident response is carried out correctly and smoothly.

The above image that shows the Incident Handling steps prepared by NIST shows that the Preparation is the first and the most important step of the Incident Response process to avoid potential incidents. The last step which is the Post-Incident Activity is also the step before the Preparation step within the Incident Response Life Cycle. This shows that the preparation step is always a progressive process, and it should be improved all the time in accordance with the experiences and the “lesson learned” after each security incident.
The preparation step covers all the preparations related to incident response processes. It covers many topics like preparation of plan/procedure/policies for incident response processes, establishment and the training of the incident response team, installing and maintaining the security tools like IPS/IDS/EDR properly, preparing equipment that would be used during incident response, training employees on social engineering, etc.
Communication
Incident responders are in constant communications with different teams and individuals during the incident response. It is of critical importance to create a list of point of contacts and their contact information that may be needed at the time of the incident response as well as to prepare the documentation that includes the critical information on who to contact with who and how to contact with these people.
It is also recommended to create a war room to be used during the cyber security incident. (War rooms are the rooms where people gather and strategies and plans are discussed to solve problems.)
Inventory List
Preparing a properly created and constantly updated inventory list will directly facilitate your incident response processes. You should have the information of all the critical systems, especially critical servers (Web servers, FTP servers, Exchange servers, SWIFT servers etc.) information should be kept updated at all times. Inventory lists that are not kept updated will impact the incident response processes critically.
Documentation
Documentation describing the incident response processes should be prepared and the incident response team should be familiar with these documentations. This will ensure that every team member will follow the plans, procedures, and policies correctly and the incident response process will go as smooth as possible.
A separate plan, policy, and procedure should be prepared for each important activity.
Network Topologies
Network topologies have critical importance to understand the activities and analyze the attack successfully during incident response.
Incident Handling Software and Hardwares
You should prepare the hardware and software that has to be utilized during the incident response in advance.
Digital Forensics Workstations and/or backup devices
Laptops
Blank removable media & hard disks
Forensics and Incident Handling Software
Preventing Incidents
The preparation step also includes the preparations for the prevention of cybersecurity incidents before they occur. Organizations should make the necessary investments in this regard and provide multi-layered protection by deploying different security solutions such as EDR, IPS/IDS, Antivirus, WAF, Firewall, DLP.
At the same time, the awareness level of employees against social engineering attacks should be increased by performing social engineering tests regularly.
Organizations must establish an official incident response capability by law. According to the documentation shared by NIST, this capability includes the following actions:
Creating an incident response policy and plan
Developing procedures for performing incident handling and reporting
Setting guidelines for communicating with outside parties regarding incidents
Selecting a team structure and staffing model
Establishing relationships and lines of communication between the incident response team and other groups, both internal (e.g., legal department) and external (e.g., law enforcement agencies)
Determining what services the incident response team should provide
Staffing and training the incident response team
Detection and Analysis
The Detection and Analysis is the step in which the cybersecurity incident is detected and investigated in depth.

(Source: NIST.SP.800-61r2)
Detection
Every cybersecurity incident starts with detection.
Cybersecurity events can be transmitted to you through different channels. For example, it can be through a triggered SIEM rule, an alert triggered by the security products you have installed, the IT team stating that the system is slowing down, or a notification sent to you via the contact form of your organization.
Verification
Things would be even easier if every detection was a cybersecurity incident, but it is not like that all the time. Instead of diving directly into the incident response process, first, the detection is to be verified and evaluated if it is indeed a cybersecurity incident or a false positive.
If you really think there is a cybersecurity incident, you should start collecting and recording the evidence. You can use the issue tracking system to record information, evidence and actions about the event. The information that should be included in the issue tracking system recommended by NIST is as follows:
The current status of the incident (new, in progress, forwarded for investigation, resolved, etc.)
A summary of the incident
Indicators related to the incident.
Other incidents related to this incident.
Actions taken by all incident handlers on this incident.
Chain of custody, if applicable
Impact assessments related to the incident.
Contact information for other involved parties (e.g., system owners, system administrators)
A list of evidence gathered during the incident investigation.
Comments from incident handlers
Next steps to be taken (e.g., rebuild the host, upgrade an application).
Since incident response information contains critical data, it is necessary to keep this information up to date at all times and to limit the number of the users who can access this information.
Prioritization
You may be exposed to more than one cybersecurity incident at the same time. The approach of responding to the cybersecurity incidents on a “first come first serve” basis is not correct. You should prioritize the incidents from the severity, criticality, impact area, potential damages, etc. perspective and start handling these incidents according to this prioritization.
You can use the categories published by NIST when prioritizing cyber security events:
Functional Impact of the Incident

Information Impact of the Incident
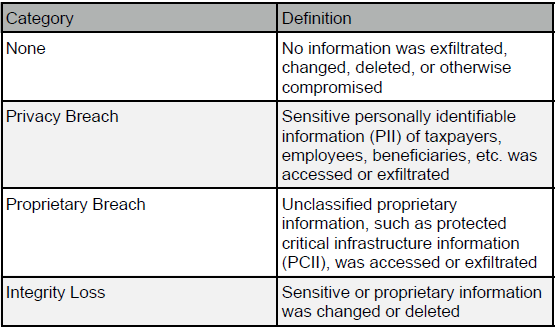
Recoverability from the Incident

Notification
After the verification of the detection, the confirmation of the cybersecurity incident and prioritization, the relevant authorities should be informed.
Analysis
The analysis step is where the activities of the attacker are analyzed. In this step, every single detail should be analyzed from the moment of attacker's first access step to his/her most recent activities on the corporate systems.
Analyzing the Root Cause
When responding to cybersecurity incidents, our priority should be to detect the attacker's access method and stop this access.
Analyzing Other Activities
During the incident response, after eliminating the possibility of the attacker to access the systems again through the initial access method, other activities should also be analyzed.
Detection & Analysis and Containment, Eradication & Recovery steps are in a continuous cycle within themselves. Devices and users found to be compromised should be isolated from the network quickly.
Containment, Eradication, and Recovery
The Containment, Eradication and Recovery step includes isolation, cleaning of the indicators/persistence methods used in the attack and restoring the systems.

(Source: NIST.SP.800-61r2)
Containment
The containment step is where the attacker is isolated so that they cannot cause any further damage. Since delaying the containment step is risky, it should be carried out as soon as the event is detected and confirmed as a cybersecurity incident.
Containment methods may change depending on the type of the cyber security incident. Some containment methods that can be applied are:
Placing the device in an isolated network segment,
Stopping the affected services,
Turning off the device,
Disconnecting the device from the network,
Disable the user’s account on the corporate network.
Eradication
The eradication step includes activities such as cleaning the malicious software left by the attacker, disabling the compromised users, deleting the users created by the attacker.
The most important point that should not be forgotten in this step is that the indicators belonging to the attack are recorded as evidence before they are deleted.
Activities to be done in the eradication step can be listed as;
Cleaning the files uploaded by the attacker,
Disabling/deleting Compromised users,
Deleting users created by the attacker,
Mitigate the identified vulnerabilities,
Termination of actively running processes.
Recovery
The recovery phase includes restoring the affected servers/devices/services to their previous operating state and confirming their proper functioning.
The recovery phase varies from organization to organization. Make sure your organization has a proper Recovery strategy.
Strategies that can be applied in the recovery phase can be listed as;
Returning to pre-compromise backup
Rebuilding systems from scratch
Replacing compromised files with clean versions
Installing patches
Changing passwords
Tightening network perimeter security
Post-Incident Activity
The Post-Incident Activity step covers the applications to be carried out after the incident response.

(Source: NIST.SP.800-61r2)
Lesson Learned
Although this step is often skipped, it is one of the most important steps. The cybersecurity incident should be evaluated from the beginning and what can be done better to avoid or prevent another cybersecurity incident should be discussed. A cybersecurity incident is inevitable, but it does not mean that we cannot learn from these incidents and be more prepared for the next incident.
A Lesson Learned meeting should be held about the cybersecurity incident with all the teams involved. The points to be discussed in the lesson learned meetings published by NIST are listed below:
What happened exactly, and at what times?
How well did staff and management perform in dealing with the incident? Were the documented procedures followed? Were they adequate?
What information was needed sooner?
Were any steps or actions taken that might have inhibited the recovery?
What would the staff and management do differently the next time a similar incident occurs?
How could information sharing with other organizations have been improved?
What corrective actions can prevent similar incidents in the future?
What precursors or indicators should be watched for in the future to detect similar incidents?
What additional tools or resources are needed to detect, analyze, and mitigate future incidents?
Last updated