ARP Poisoning/Spoofing
ARP Poisoning/Spoofing (Man In The Middle Attack)
ARP protocol, or Address Resolution Protocol (ARP), is the technology responsible for allowing devices to identify themselves on a network. Address Resolution Protocol Poisoning (also known as ARP Spoofing or Man In The Middle (MITM) attack) is a type of attack that involves network jamming/manipulating by sending malicious ARP packets to the default gateway. The ultimate aim is to manipulate the "IP to MAC address table" and sniff the traffic of the target host.
There are a variety of tools available to conduct ARP attacks. However, the mindset of the attack is static, so it is easy to detect such an attack by knowing the ARP protocol workflow and Wireshark skills.
ARP analysis in a nutshell:
Works on the local network
Enables the communication between MAC addresses
Not a secure protocol
Not a routable protocol
It doesn't have an authentication function
Common patterns are request & response, announcement and gratuitous packets.
Before investigating the traffic, let's review some legitimate and suspicious ARP packets. The legitimate requests are similar to the shown picture: a broadcast request that asks if any of the available hosts use an IP address and a reply from the host that uses the particular IP address.
Global search
arp
"ARP" options for grabbing the low-hanging fruits:
Opcode 1: ARP requests.
Opcode 2: ARP responses.
Hunt: Arp scanning
Hunt: Possible ARP poisoning detection
Hunt: Possible ARP flooding from detection:
arp.opcode == 1arp.opcode == 2arp.dst.hw_mac==00:00:00:00:00:00arp.duplicate-address-detected or arp.duplicate-address-frame((arp) && (arp.opcode == 1)) && (arp.src.hw_mac == target-mac-address)

A suspicious situation means having two different ARP responses (conflict) for a particular IP address. In that case, Wireshark's expert info tab warns the analyst. However, it only shows the second occurrence of the duplicate value to highlight the conflict. Therefore, identifying the malicious packet from the legitimate one is the analyst's challenge. A possible IP spoofing case is shown in the picture below.

Here, knowing the network architecture and inspecting the traffic for a specific time frame can help detect the anomaly. As an analyst, you should take notes of your findings before going further. This will help you be organised and make it easier to correlate the further findings. Look at the given picture; there is a conflict; the MAC address that ends with "b4" crafted an ARP request with the "192.168.1.25" IP address, then claimed to have the "192.168.1.1" IP address.
Notes
Detection Notes
Findings
Possible IP address match.
1 IP address announced from a MAC address.
MAC: 00:0c:29:e2:18:b4
IP: 192.168.1.25
Possible ARP spoofing attempt.
2 MAC addresses claimed the same IP address (192.168.1.1). The " 192.168.1.1" IP address is a possible gateway address.
MAC1: 50:78:b3:f3:cd:f4
MAC 2: 00:0c:29:e2:18:b4
Possible ARP flooding attempt.
The MAC address that ends with "b4" claims to have a different/new IP address.
MAC: 00:0c:29:e2:18:b4
IP: 192.168.1.1
Let's keep inspecting the traffic to spot any other anomalies. Note that the case is split into multiple capture files to make the investigation easier.

At this point, it is evident that there is an anomaly. A security analyst cannot ignore a flood of ARP requests. This could be malicious activity, scan or network problems. There is a new anomaly; the MAC address that ends with "b4" crafted multiple ARP requests with the "192.168.1.25" IP address. Let's focus on the source of this anomaly and extend the taken notes.
Notes
Detection Notes
Findings
Possible IP address match.
1 IP address announced from a MAC address.
MAC: 00:0c:29:e2:18:b4
IP: 192.168.1.25
Possible ARP spoofing attempt.
2 MAC addresses claimed the same IP address (192.168.1.1).The " 192.168.1.1" IP address is a possible gateway address.
MAC1: 50:78:b3:f3:cd:f4
MAC 2: 00:0c:29:e2:18:b4
Possible ARP spoofing attempt.
The MAC address that ends with "b4" claims to have a different/new IP address.
MAC: 00:0c:29:e2:18:b4
IP: 192.168.1.1
Possible ARP flooding attempt.
The MAC address that ends with "b4" crafted multiple ARP requests against a range of IP addresses.
MAC: 00:0c:29:e2:18:b4
IP: 192.168.1.xxx
Up to this point, it is evident that the MAC address that ends with "b4" owns the "192.168.1.25" IP address and crafted suspicious ARP requests against a range of IP addresses. It also claimed to have the possible gateway address as well. Let's focus on other protocols and spot the reflection of this anomaly in the following sections of the time frame.
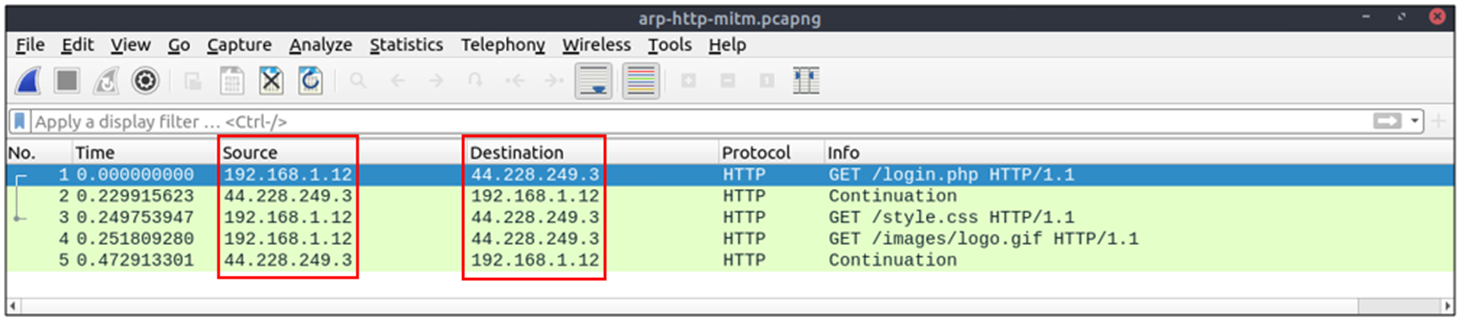
There is HTTP traffic, and everything looks normal at the IP level, so there is no linked information with our previous findings. Let's add the MAC addresses as columns in the packet list pane to reveal the communication behind the IP addresses.

One more anomaly! The MAC address that ends with "b4" is the destination of all HTTP packets! It is evident that there is a MITM attack, and the attacker is the host with the MAC address that ends with "b4". All traffic linked to "192.168.1.12" IP addresses is forwarded to the malicious host. Let's summarise the findings before concluding the investigation.
Detection Notes
Findings
IP to MAC matches.
3 IP to MAC address matches.
MAC: 00:0c:29:e2:18:b4 = IP: 192.168.1.25
MAC: 50:78:b3:f3:cd:f4 = IP: 192.1681.1
MAC: 00:0c:29:98:c7:a8 = IP: 192.168.1.12
Attacker
The attacker created noise with ARP packets.
MAC: 00:0c:29:e2:18:b4 = IP: 192.168.1.25
Router/gateway
Gateway address.
MAC: 50:78:b3:f3:cd:f4 = IP: 192.1681.1
Victim
The attacker sniffed all traffic of the victim.
MAC: 50:78:b3:f3:cd:f4 = IP: 192.1681.12
Detecting these bits and pieces of information in a big capture file is challenging. However, in real-life cases, you will not have "tailored data" ready for investigation. Therefore you need to have the analyst mindset, knowledge and tool skills to filter and detect the anomalies.
Last updated