FTP
Cleartext Protocol Analysis
Investigating cleartext protocol traces sounds easy, but when the time comes to investigate a big network trace for incident analysis and response, the game changes. Proper analysis is more than following the stream and reading the cleartext data. For a security analyst, it is important to create statistics and key results from the investigation process. As mentioned earlier at the beginning of the Wireshark room series, the analyst should have the required network knowledge and tool skills to accomplish this. Let's simulate a cleartext protocol investigation with Wireshark!
FTP Analysis
File Transfer Protocol (FTP) is designed to transfer files with ease, so it focuses on simplicity rather than security. As a result of this, using this protocol in unsecured environments could create security issues like:
MITM attacks
Credential stealing and unauthorized access
Phishing
Malware planting
Data exfiltration
FTP analysis in a nutshell:
Global search
ftp
"FTP" options for grabbing the low-hanging fruits:
x1x series: Information request responses.
x2x series: Connection messages.
x3x series: Authentication messages.
Note: "200" means command successful.
---
"x1x" series options for grabbing the low-hanging fruits:
211: System status.
212: Directory status.
213: File status
ftp.response.code == 211
"x2x" series options for grabbing the low-hanging fruits:
220: Service ready.
227: Entering passive mode.
228: Long passive mode.
229: Extended passive mode.
ftp.response.code == 227
"x3x" series options for grabbing the low-hanging fruits:
230: User login.
231: User logout.
331: Valid username.
430: Invalid username or password
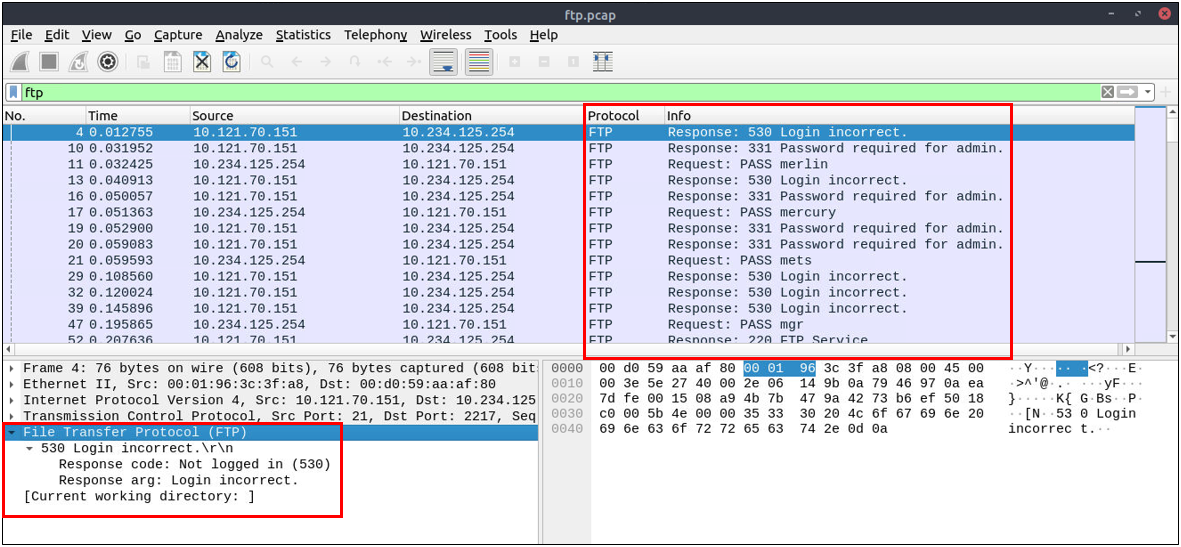
530: No login, invalid password.
ftp.response.code == 230
"FTP" commands for grabbing the low-hanging fruits:
USER: Username.
PASS: Password.
CWD: Current work directory.
LIST: List.
ftp.request.command == "USER"ftp.request.command == "PASS"ftp.request.arg == "password"
Advanced usages examples for grabbing low-hanging fruits:
Bruteforce signal: List failed login attempts.
Bruteforce signal: List target username.
Password spray signal: List targets for a static password.
ftp.response.code == 530(ftp.response.code == 530) and (ftp.response.arg contains "username")(ftp.request.command == "PASS" ) and (ftp.request.arg == "password")
Last updated