Creating Security Rules (firewall)
Actionable Results!
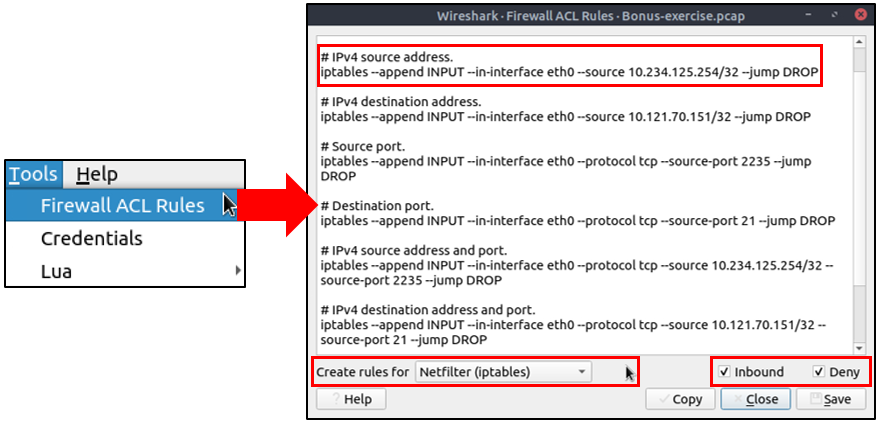
You have investigated the traffic, detected anomalies and created notes for further investigation. What is next? Not every case investigation is carried out by a crowd team. As a security analyst, there will be some cases you need to spot the anomaly, identify the source and take action. Wireshark is not all about packet details; it can help you to create firewall rules ready to implement with a couple of clicks. You can create firewall rules by using the "Tools --> Firewall ACL Rules" menu. Once you use this feature, it will open a new window and provide a combination of rules (IP, port and MAC address-based) for different purposes. Note that these rules are generated for implementation on an outside firewall interface.
Currently, Wireshark can create rules for:
Netfilter (iptables)
Cisco IOS (standard/extended)
IP Filter (ipfilter)
IPFirewall (ipfw)
Packet filter (pf)
Windows Firewall (netsh new/old format)
Last updated